Risk Management
- Policies and Procedures — In order to ensure the stable operation and sustainable development of the company, this regulation was specially formulated and approved by the board of directors on August 10, 2021 to establish an overall risk management system. The company's board of directors, audit committee, general manager and general manager's office, the audit office, various units and subsidiaries jointly participate in the promotion of implementation.
- Risk Management Category — The risks faced by the company are divided into four major areas: operation, finance, environment and operations. The risk management group and relevant departments identify potential risks related to operations through risk management meetings.
- Risk Management Organization — (1) Audit Committee and Board of Directors (2) General Manager and General Manager Office (3) Audit Office (4) Units and subsidiaries
- Risk Management Process
 |
|
Risk Management Working Group
|
|
 |
|
-
Goals
- In response to the requirements of corporate governance laws and regulations, introduce an enterprise risk management mechanism
- Refer to "ISO 31000 Risk Management -Principles and Guidelines" to perform enterprise risk analysis and assessment
- Comply with Task Force on Climate-related Financial Disclosures (TCFD) requirements (including governance, strategy, risk management, indicators and targets)
- Disclose relevant information in compliance with GRI and customer requirements
Operation of risk management

|
Item |
Description |
|
Operational Risk |
The company conducts group operation management review meetings every month to identify and deal with operational risks. |
|
Financial Risk |
The company is registered in the Cayman Islands and has no real economic activities. Its main operations are in mainland China and Taiwan. The Group's business operations are carried out in accordance with important policies and laws and regulations at home and abroad. Always pay attention to important policies and laws in the country and region where it is located For information about changes, preventive preparations should be made as early as possible through various channels. If there are changes, consult with lawyers, accountants and other relevant units, or entrust them to evaluate and plan response measures, so as to respond to market changes in a timely manner and take appropriate response measures. |
|
Job Risk |
The company continues to carry out "information security management", aiming at improving the information security risk management structure, information security policies, specific management plans, and resources invested in information security management. |
|
Environmental Risk |
The company has established the AES Sustainability Committee on 2022/10/12 to continue to implement solutions to issues such as circular economy, green innovation, caring for society, and integrity. |
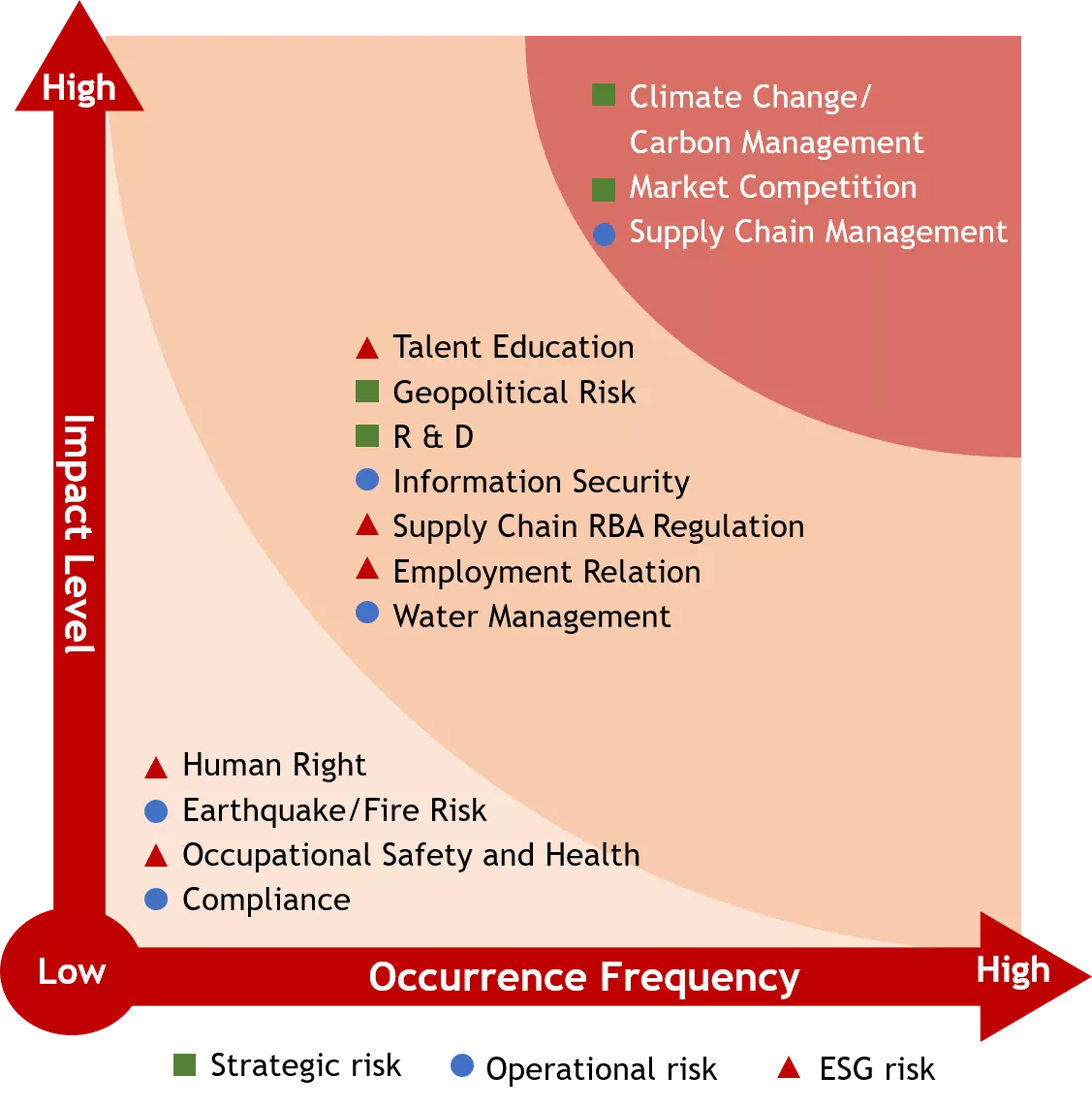
Corporate Risk Identification
|
|
|
Risk Response Approach
1. Climate Change/ Carbon Management: refer to Environmental Sustainability " Climate Change"
2. Market Competition: refer to Products
3. Supply Chain Management: refer to Supply Chain Management " Sustainable Supply Chain Management Policy"
Information security management
2. Information Security Policy : To protect the company's information assets from deliberate or accidental destruction and ensure sustainable business operations, the Information Security Policy is established to confirm the security of the company's important information assets, including: Confidentiality: Ensuring that only authorized users can access information. Integrity: Ensuring the correctness and completeness of information and information processing methods. Availability: Ensuring that authorized users can access information and related assets in a timely manner when needed. Through the management of this policy, the company clearly declares its support for information security goals, provides guidelines for relevant personnel, and appropriately meets the company's requirements for information security and relevant legal regulations, thereby reducing the impact of any information security incidents and ensuring the company's and customers' rights and interests.
3. Specific Information Security Management Plan : The company's information department has developed an information system management procedure that applies to the use of the company's computer information systems and enterprise network resources, with the aim of ensuring the correctness and security of the company's information data through the implementation of this procedure and the implementation of regulations by colleagues, providing management information, and assisting in data processing by various units. The main contents of the management procedure include the following:
(1) Use and cancellation of computer system resources: Regulations on the control requirements for colleagues' use of computer system resources required for work, including the use application of PCs/NBs, installation of computer software, control of the internet access function of official NBs taken outside the factory, and the cancellation of the computer resource usage rights and accounts of departing employees.
(2) Data Backup and Disaster Recovery : This section describes the backup policies and requirements for data backup operations, including setting backup schedules for server files and database backups to tape or offsite hard drives. The backup software will notify the management team via email if backup tasks are successful or not. The management team must respond immediately to address and resolve any backup failures, ensuring that the backups are completed correctly. Disaster recovery testing is required every six months and is the responsibility of the relevant department.
(3) Computer Virus Management: This section outlines the company's approach to preventing computer viruses, including the installation of authorized antivirus software on all computers, periodic updates to virus definitions, and regular system and security updates via the Windows Update server. Proxy and firewall controls are used to manage Internet behavior.
(4) Email Management: This section includes rules for using email, such as managing the number of recipients, the size of individual emails, and the handling of personal and external company emails .
(5) Internet Usage Management: This section describes the rules for applying for and using the Internet, prohibiting browsing and gaming, shopping, audio, gambling, social media, illegal or violent websites, advertisements, adult content, free Internet resources, and controversial and dubious websites. (6) Remote Access Management: This section outlines the requirements for using VPN to access internal services from outside the company network. VPN access requires an application and a personal mobile device with OTP dual-factor authentication. The IT department checks VPN usage regularly and deactivates accounts that have not been accessed for over six months.
(7) Information Room Management: This section specifies the access control requirements for information rooms and daily operations, including temperature and humidity control, UPS continuous power supply systems, environmental and equipment status checks, and automatic notifications of abnormal events.
(8) Education and training : The company will provide basic information security education and training to the new employees of the company when they enter the company. In addition, for employees who are currently working, information security promotions must be conducted through the company's internal portal website or emails from time to time, including email security, Internet security, and remote security operations, etc.
(II) The company adheres to the PDCA (Plan-Do-Check-Act) principles of the ISO 27001 management system for information security management. It has established the positions of an information security manager and an information security specialist in compliance with the regulations of the relevant authority. Regular annual reviews of regulatory documents are conducted, along with biannual vulnerability scans and subsequent remediation efforts. Upon discovery of a vulnerability, a review is conducted to confirm its effectiveness, and an information security management review meeting is held at least once a year to facilitate continuous review and improvement.
(III) Losses suffered, potential impact and response measures due to significant information and communication security incidents, as well as the impact and response measures of information and communication security risks on the company's financial and business operations: The Company did not experience any significant security incidents in 2022 that resulted in operational damage.
 Contact us
Contact us